Computer Networks

Computer Network
Page bookmarks
Network Use-Cases
Computer networks can be used for a variety of purposes, such as:
- Sharing files between computers
- Printing to a shared printer
- Playing online games
- Streaming movies and music
- Accessing the Internet
Network Types
There are two main types of computer networks: local area networks (LANs) and wide area networks (WANs).
LANs are networks that are confined to a small area, such as a home, office, or school. WANs are networks that cover a large area, such as a city, state, or country.
Computer networks are an essential part of modern life. They allow us to connect with people all over the world and access information and resources that would not be available to us otherwise.
Network Components
Computer networks are made up of different components, such as:
- Nodes
- Links
- Protocols
Nodes are the individual computers that are connected to the network. Links are the connections between the nodes. Protocols are the rules that govern how the nodes communicate with each other.
Network Devices
There are a number of different devices that are required to create a small computer network. These devices include:
- Modem
- Router
- Switch
- Wireless Access Point
- Ethernet Cables
The modem is the device that connects your network to the Internet. The router is the device that controls the traffic on your network. The switch is the device that connects multiple devices on your network together. The wireless access point is the device that allows you to connect wireless devices to your network. The Ethernet cables are the cables that connect the devices on your network together.
In addition to these devices, you may also need to purchase a firewall, a security camera, or a NAS (network-attached storage) device.
The specific devices that you need will depend on the size and complexity of your network.
Overview
Here is a brief overview of each of the devices:
- Modem: A modem is a device that converts digital signals into analog signals and vice versa. This allows your computer to communicate with your Internet service provider (ISP).
- Router: A router is a device that controls the traffic on your network. It determines which devices can communicate with each other and how they can communicate.
- Switch: A switch is a device that connects multiple devices on your network together. It allows the devices to communicate with each other directly, without having to go through the router.
- Wireless Access Point: A wireless access point is a device that allows you to connect wireless devices to your network. It creates a wireless network that your devices can connect to.
- Ethernet Cables: Ethernet cables are the cables that connect the devices on your network together. They are used to connect wired devices to your network.
Once you have purchased the necessary devices, you will need to configure them. The configuration process will vary depending on the devices that you have purchased.
Once the devices are configured, you will be able to connect your devices to your network. You can then start sharing files, printers, and other resources.
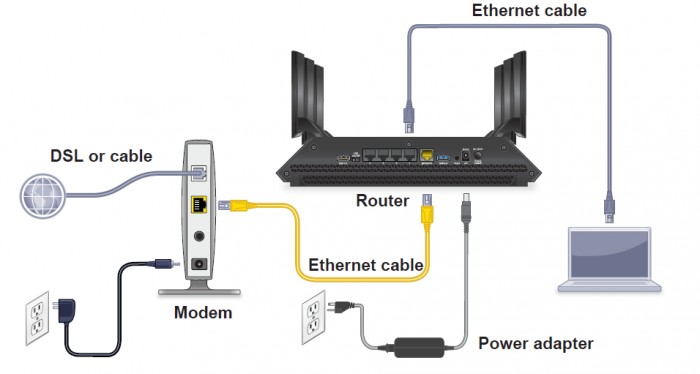
Network Setup
Network Nodes
All computers in a network are called nodes. Some nodes are connected with ethernet ehires, some other computer can be portable devices or TV connected using wireless communication wi-fi. All nodes have a unique name in a network and nodes can communicate to each other. You can chose two configurations:
peer-to-peer (P2P)
A peer-to-peer (P2P) network is a type of network in which each computer acts as both a client and a server. This means that any computer on the network can share its resources with any other computer on the network.
Server based
A server-based star network is a type of network in which there is a central server that controls the network. All of the other computers on the network are clients that connect to the server to access resources.
Config Comparison
Here is a table that summarizes the key differences between P2P networks and server-based star networks:
| Feature | Peer-to-Peer Network | Server-Based Star Network |
|---|---|---|
| Centralization | No central server | There is a central server |
| Scalability | Difficult to scale | Easy to scale |
| Security | Less secure | More secure |
| Cost | Lower cost | Higher cost |
P2P networks are often used for file sharing, gaming, and collaboration. Server-based star networks are often used for email, web browsing, and file sharing.
The best type of network for you will depend on your specific needs. If you need a network that is easy to scale and secure, then a server-based star network is a good choice. If you need a network that is low-cost and easy to set up, then a P2P network is a good choice.
Internet WAN
Internet Connection
There are a number of different ways to connect a local network to the WAN network Internet. These methods include:
- Dial-up
- DSL
- Cable
- Fiber optic
- Ethernet
The best method for you will depend on your specific needs and requirements.
Overview
Here is a brief overview of each of the methods:
- Dial-up: Dial-up is the oldest and most basic method of connecting to the Internet. It uses a telephone line to connect your computer to the Internet. Dial-up is a slow and unreliable method of connecting to the Internet.
- DSL: DSL is a digital subscriber line. It uses the same telephone line as dial-up, but it provides a much faster connection. DSL is a good option for people who want a faster connection than dial-up but don't want to pay for cable or fiber optic.
- Cable: Cable is a type of broadband connection that uses the same coaxial cables as cable television. Cable is a fast and reliable connection. It is a good option for people who want a fast and reliable connection for gaming, streaming video, or other bandwidth-intensive activities.
- Fiber optic: Fiber optic is the fastest type of broadband connection. It uses light signals to transmit data, which is much faster than copper wires. Fiber optic is a good option for people who need the fastest possible connection for business or other demanding applications.
- Ethernet: Ethernet is a wired connection that uses Ethernet cables to connect your computer to the Internet. Ethernet is a reliable and secure connection. It is a good option for businesses and other organizations that need a secure connection.
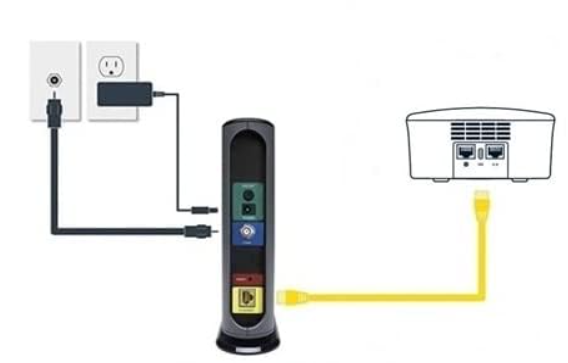
DSL Modem + Wi-fi Router
Once you have chosen a method for connecting your local network to the WAN network Internet, you will need to purchase the necessary hardware. This hardware will vary depending on the method that you choose.
Once you have purchased the necessary hardware, you will need to configure it. The configuration process will vary depending on the method that you choose.
Once the hardware is configured, you will be able to connect your local network to the WAN network Internet.
Network Protocol
A network protocol is a set of rules that govern how devices communicate with each other on a network.
Protocols define the format of data that is exchanged between devices, as well as the way that data is transmitted.
Without protocols, devices would not be able to understand each other and communication would not be possible.
There are many different network protocols, each of which is used for a specific purpose. Some of the most common network protocols include:
- Transmission Control Protocol (TCP)
- Internet Protocol (IP)
- Hypertext Transfer Protocol (HTTP)
- Simple Mail Transfer Protocol (SMTP)
- File Transfer Protocol (FTP)
TCP and IP are the two most important network protocols. TCP is responsible for ensuring that data is delivered reliably, while IP is responsible for routing data between devices on a network.
HTTP is the protocol that is used to transfer web pages over the Internet. SMTP is the protocol that is used to send email messages. FTP is the protocol that is used to transfer files between devices on a network.
Network protocols are essential for the operation of the Internet. Without protocols, the Internet would not be able to function.
TCP/IP Protocol
Transmission Control Protocol/Internet Protocol (TCP/IP) is a set of networking protocols that define how computers communicate over the Internet. TCP/IP is the foundation of the Internet and is used by all devices that connect to the Internet.
TCP/IP is a layered protocol, which means that it is divided into different layers. Each layer has a specific function, and the layers work together to ensure that data is transmitted reliably and efficiently.
The four layers of TCP/IP are:
- Physical layer: This layer is responsible for the physical transmission of data over a network.
- Data link layer: This layer is responsible for error detection and correction.
- Network layer: This layer is responsible for routing data between networks.
- Transport layer: This layer is responsible for ensuring that data is delivered reliably.
TCP/IP is a complex protocol, but it is essential for the operation of the Internet. Without TCP/IP, the Internet would not be able to function.
Here are some of the benefits of TCP/IP:
- Reliability: TCP/IP ensures that data is delivered reliably.
- Efficiency: TCP/IP is a very efficient protocol.
- Scalability: TCP/IP can scale to handle large amounts of traffic.
- Interoperability: TCP/IP is interoperable with other protocols.
TCP/IP is the most widely used protocol on the Internet. It is used by all devices that connect to the Internet, including computers, smartphones, and routers.
If you are interested in learning more about TCP/IP, there are many resources available online and in libraries.
Name Server
A name server is a computer that translates domain names into IP addresses. Domain names are the human-readable addresses of websites, such as www.google.com. IP addresses are the numerical addresses of websites, such as 172.217.16.238.
When you type a domain name into your web browser, your computer sends a request to a name server. The name server then looks up the domain name in its database and returns the corresponding IP address. Your computer then uses the IP address to connect to the website.
There are two main types of name servers: root name servers and top-level domain (TLD) name servers. Root name servers are the top-level servers in the DNS hierarchy. They store the addresses of all of the TLD name servers. TLD name servers store the addresses of all of the websites within their domain.
Name servers are essential for the operation of the Internet. Without name servers, it would be impossible to remember the numerical addresses of websites.
Here are some of the benefits of name servers:
- Easy to remember: Domain names are much easier to remember than IP addresses.
- Scalable: The DNS hierarchy can be scaled to handle large amounts of traffic.
- Reliable: Name servers are designed to be highly reliable.
Name servers are an essential part of the Internet. They allow us to access websites by their domain names, which makes it much easier to remember and use them.
IP Address
An IP address is a unique identifier for a device on a network. It is a 32-bit number that is divided into four octets. Each octet is a number between 0 and 255.
A network mask is a 32-bit number that is used to determine which part of an IP address belongs to the network and which part belongs to the host. The network mask is usually written in CIDR notation, which is a format that uses a slash followed by a number. The number indicates how many of the bits in the network mask are used to identify the network.
For example, the IP address 192.168.1.100 and the network mask 255.255.255.0 identify the same host on the network. The first three octets of the IP address (192.168.1) identify the network, and the last octet (100) identifies the host.
IP addresses and network masks are essential for routing data on a network. When a packet of data is sent from one device to another, the router uses the IP address and network mask to determine which network the packet should be sent to.
Here are some of the benefits of IP addresses and network masks:
- Unique identification: IP addresses uniquely identify devices on a network.
- Routing: IP addresses and network masks are used to route data on a network.
- Security: IP addresses and network masks can be used to control access to a network.
IP addresses and network masks are an essential part of networking. They allow devices to communicate with each other on a network and they help to secure the network.
IP Type
There are two types of IP addresses: fixed IP addresses and dynamic IP addresses. You must understand the differences because you need to configure the network nodes. In a simple network the nodes are automaticly configured but in a complex network the IP must be manually assigned for each server.
1. A fixed IP address is an IP address that does not change. This means the device will always have the same IP address when it is connected to the network. Fixed IP addresses are often used for servers and other devices that need to be accessible from the internet.
A dynamic IP address is an IP address that changes every time the device connects to the network. This is the most common type of IP address and is used for most home and office devices. Dynamic IP addresses are assigned by the internet service provider (ISP) and are usually changed every time the device is rebooted or disconnected from the network.
Dynamic vs Fixed IP
Here is a table that summarizes the key differences between fixed IP addresses and dynamic IP addresses:
| Feature | Fixed IP Address | Dynamic IP Address |
|---|---|---|
| IP address | Does not change | Changes every time the device connects to the network |
| Use | Servers, devices that need to be accessible from the internet | Most home and office devices |
| Advantages | Easy to remember, more secure | More flexible, easier to manage |
| Disadvantages | More difficult to manage, less flexible | Can be less secure |
The best type of IP address for you will depend on your specific needs. If you need a device to be accessible from the internet and you want to make sure that the IP address does not change, then you should use a fixed IP address. If you need a device that is easy to manage and you do not need the IP address to be constant, then you should use a dynamic IP address.
IP Routing
IP routing is the process of determining the best path for a packet of data to travel from its source to its destination. Routers are devices that use IP routing to forward packets of data between networks.
When a router receives a packet of data, it looks at the destination IP address of the packet and determines the best path for the packet to travel. The router then forwards the packet to the next router in the path, and the process repeats until the packet reaches its destination.
A port is a number that identifies a specific service or application on a computer. When a router forwards a packet of data, it also specifies the port number that the packet should be sent to. This allows the router to forward the packet to the correct application on the destination computer.
There are two main types of IP routing: static routing and dynamic routing. Static routing is when the router's routing table is manually configured. Dynamic routing is when the router's routing table is automatically updated based on network traffic.
IP routing is essential for the operation of the Internet. Without IP routing, packets of data would not be able to travel from their source to their destination.
Here are some of the benefits of IP routing:
- Efficiency: IP routing can help to ensure that packets of data are routed efficiently.
- Scalability: IP routing can be scaled to handle large amounts of traffic.
- Security: IP routing can be used to control access to networks.
- Port: Ports allow routers to forward packets of data to the correct application on the destination computer.
IP routing is an essential part of networking. It allows devices to communicate with each other on a network and it helps to secure the network.
What is a Firewall?
A firewal is securitya network system that monitors and controls incoming and outgoing network traffic. Firewals are used to protect networks from unauthorized access, viruses, and other threats.
There are two main types of firewalls: packet-filtering firewalls and stateful firewalls. Packet-filtering firewalls examine the headers of network packets to determine whether they should be allowed to pass through the firewall. Stateful firewalls examine the headers of network packets as well as the state of the connection between the two computers.
Firewalls can be implemented in hardware or software. Hardware firewalls are dedicated devices that are specifically designed for firewalling. Software firewalls are programs that are installed on computers.
Firewalls are an essential part of network security. They help to protect networks from unauthorized access, viruses, and other threats. Here are some of the benefits of using a firewall:
- Protection from unauthorized access: Firewalls can help to prevent unauthorized users from accessing your network.
- Protection from viruses: Firewalls can help to prevent viruses from entering your network.
- Protection from other threats: Firewalls can help to protect your network from other threats, such as denial-of-service attacks.
If you are concerned about the security of your network, you should consider using a firewall. Firewalls can help to protect your network from unauthorized access, viruses, and other threats.
Ethernet CAT Cables
Ethernet CAT cables are a type of twisted-pair cable that is commonly used for Ethernet connections. They are made up of four pairs of copper wires that are twisted together to reduce interference. CAT cables are rated according to their performance capabilities, with CAT5 being the most common type.
Here is a table of different types of CAT cables, their speed description, and use-case:
| CAT Cable Type | Speed | Use-Case |
|---|---|---|
| CAT5 | 100 Mbps | Basic Ethernet networking, VoIP, and file sharing |
| CAT5e | 100 Mbps to 1 Gbps | Fast Ethernet networking, Gigabit Ethernet networking, and VoIP |
| CAT6 | 1 Gbps to 10 Gbps | Gigabit Ethernet networking, 10 Gigabit Ethernet networking, and video streaming |
| CAT6a | 10 Gbps to 40 Gbps | 10 Gigabit Ethernet networking, 40 Gigabit Ethernet networking, and enterprise applications |
| CAT7 | 10 Gbps to 100 Gbps | 10 Gigabit Ethernet networking, 40 Gigabit Ethernet networking, 100 Gigabit Ethernet networking, and enterprise applications |
As you can see, the different types of CAT cables offer different speeds and are suited for different use cases. CAT5 is the most common type of CAT cable and is suitable for basic Ethernet networking. CAT5e offers faster speeds and is suitable for Gigabit Ethernet networking. CAT6 and CAT6a offer even faster speeds and are suitable for 10 Gigabit Ethernet networking and enterprise applications. CAT7 offers the fastest speeds and is suitable for 100 Gigabit Ethernet networking and enterprise applications.

Ethernet Connectors
When choosing a CAT cable, it is important to consider the speed requirements of your network and the type of applications that you will be using. If you are not sure which type of CAT cable to choose, it is always best to consult with a networking professional.
Wireless Protocol
Wireless protocols are the standards that govern how devices communicate wirelessly. There have been several generations of wireless protocols developed over the years, each with its own set of features and performance capabilities.
The following table lists the different generations of wireless protocols, along with their performance and description:
| Generation | Performance | Description |
|---|---|---|
| 1G | 1 Mbps | The first generation of wireless protocols. It was used for voice calls and data transfer. |
| 2G | 14 Mbps | The second generation of wireless protocols. It was used for voice calls, data transfer, and text messaging. |
| 3G | 21 Mbps | The third generation of wireless protocols. It was used for voice calls, data transfer, text messaging, and video streaming. |
| 4G | 100 Mbps | The fourth generation of wireless protocols. It is used for voice calls, data transfer, text messaging, video streaming, and gaming. |
| 5G | 10 Gbps | The fifth generation of wireless protocols. It is the fastest wireless protocol available. It is used for voice calls, data transfer, text messaging, video streaming, gaming, and augmented reality. |
As you can see, each generation of wireless protocols has offered improved performance over the previous generation. This has allowed for new and innovative applications to be developed, such as video streaming and gaming.
The latest generation of wireless protocols, 5G, is the fastest wireless protocol available. It offers speeds of up to 10 Gbps, which is 100 times faster than 4G. 5G is being used for a variety of applications, including voice calls, data transfer, text messaging, video streaming, gaming, and augmented reality.
As wireless technology continues to evolve, we can expect to see even faster speeds and new and innovative applications.
Wi-Fi Generations
Wi-Fi is a wireless networking technology that allows devices to connect to the internet or to each other without the need for cables. There have been several generations of Wi-Fi developed over the years, each with its own set of features and performance capabilities.
The following table lists the different generations of Wi-Fi, along with their year of introduction, performance, and description:
| Generation | Year | Performance | Frequency | Description |
|---|---|---|---|---|
| 802.11b | 1999 | 11 Mbps | 2.4 GHz | The first generation of Wi-Fi. It was used for basic internet browsing and file sharing. |
| 802.11a | 1999 | 54 Mbps | 5 GHz | A faster version of 802.11b that was designed for use in unlicensed spectrum. |
| 802.11g | 2003 | 54 Mbps | 2.4 GHz | A backward-compatible version of 802.11a that offered improved performance in the 2.4 GHz band. |
| 802.11n | 2009 | 600 Mbps | 2.4 GHz and 5 GHz | A major improvement over previous Wi-Fi generations that offered faster speeds and better range. |
| 802.11ac | 2014 | 1.3 Gbps | 2.4 GHz and 5 GHz | Another major improvement over previous Wi-Fi generations that offered even faster speeds and better range. |
| 802.11ax | 2019 | 9.6 Gbps | 2.4 GHz and 5 GHz | The latest generation, Wi-Fi 6 that offers the fastest speeds and best range yet. |
As you can see, each generation of Wi-Fi has offered improved performance over the previous generation. This has allowed for new and innovative applications to be developed, such as streaming video and online gaming.

Industrial 5G Router
The latest generation of Wi-Fi, 802.11ax, is the fastest Wi-Fi available. It offers speeds of up to 9.6 Gbps, which is 100 times faster than 802.11b. 802.11ax is being used for a variety of applications, including streaming video, online gaming, and virtual reality.
As Wi-Fi technology continues to evolve, we can expect to see even faster speeds and new and innovative applications.
You are ready: Go back & take the exam.
